Abstract: This article describes the security key technologies required for automotive ADAS and V2X.
This article refers to the address: http://
The Advanced Driver Assistance System (ADAS) allows the driver to better understand the situation and control, making driving easier and safer. ADAS technology can be based on in-vehicle systems, ie vehicle resident systems such as vision camera systems and sensor technology, or based on intelligent interconnection networks such as vehicles and vehicles (V2V) or vehicle and infrastructure (V2I) systems. The two are collectively referred to as V2X.
V2X communication utilizes an in-vehicle system for short-range wireless communication devices to transmit safety-related information such as vehicle speed, direction, braking state, and vehicle size with other vehicles. The V2X network can transmit information over long distances by using multiple hops to transmit information through other nodes. This farther detection range allows you to look beyond the corners or through the capabilities of other vehicles, helping vehicles equipped with V2X to detect certain threats faster than sensors, cameras or radars and alerting the driver accordingly.
In addition to developing basic security information for security applications, the network can also be used by other connected vehicle applications, such as mobility or weather. Additional information from vehicles or infrastructure can be developed in the future.
In terms of safety impact, according to a study conducted in 2004-2008, the US Highway Traffic Safety Administration (NHTSA) estimated that the use of V2C networks could avoid 22 possible vehicle collision scenarios, which means that nearly 81 can be avoided. % of undamaged light car collisions.
According to the vehicle collision data from 2004 to 2008, the death, injury and property losses caused by the collision of these 22 target light vehicles each year averaged about 27,000, 1.8 million and 7.3 million respectively.
Large-scale adoption of V2I can bring potential huge security advantages, such as red light warning, corner speed warning, parking sign clearance assistance, deceleration zone warning, on-site weather information warning, violation of parking sign warning, violation of railway warning, excessive Vehicle warnings, etc.
The warning not only informs the vehicle and the driver that the safety is violated, but also alerts the nearby vehicle via a wireless link to help prevent collisions, such as when the vehicle is at a red corner of the intersection or when the parking sign is violated.
V2X security
In order to fully realize the potential of V2X, the system must ensure two points: the information comes from a trusted source; and the information has not been tampered with from the sender to the receiver.
Among the two points mentioned above, if any one is not done well, it will cause problems, causing serious consequences and fatality. False information can provide vehicle driving data such as the wrong speed and direction, which can lead to accidents. The manipulation of data by illegal elements can lead to urban traffic disruption and confusion.
In addition to the concerns mentioned above, users are also concerned about privacy and to ensure that information does not reveal the identity and location of the driver. Anonymous vehicle safety information is only provided to pre-authorized entities, such as other vehicles. To ensure large-scale adoption of V2X, users must rely on V2X systems to not provide their personal data, which is especially important.
In order to prove reliability, the sender of the message must provide a unique identifier that the recipient can verify, proving that the information comes from a reliable source. In general, this is achieved by using symmetric or asymmetric encryption techniques (Figure 1).
Symmetric encryption is typically suitable for small networks with a limited number of nodes, where the sender and receiver share a common key that is normally known to both parties before any packet is transmitted. By dynamically generating a code (called a message authentication code, or macs) based on the payload and key calculations to verify the integrity and source of the packet, the recipient verifies the authenticity of the data with the key.
Although this method is simple, since all nodes must use the same key, there is an unacceptable security risk. However, if each pair of nodes that communicate with each other must use different keys, it is difficult to handle. This method is not possible for large networks such as large V2X.
Asymmetric encryption provides an extensible way to connect as many nodes as possible in the network. To achieve this, each node digitally signs each delivered message using a private key. The digital signature can be verified by the recipient using the associated public key transmitted to all receiving nodes. In addition to having better scalability than symmetric encryption, asymmetric encryption enables simpler fault node replacement.
However, this raises another question: How to ensure that the private and public keys used by each node are real and not tampered with?
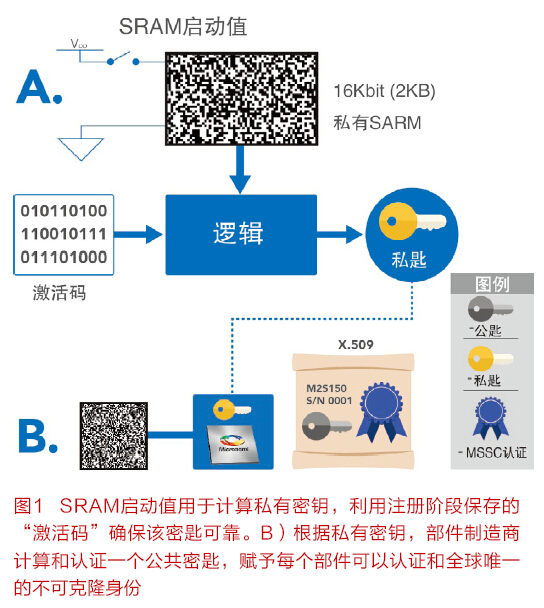
The best solution to the first part of the problem is to use the biometric signature of the silicon IC, which is built on tiny physical changes in the manufacturing process of each device. These process changes can never be exactly the same, providing a unique signature for each device, so no one can clone two ICs. This signature is called a physical unclonable function (PUF). In addition to being non-cloned, PUF-based keys are usually implemented at the atomic level and are therefore difficult to extract by hackers. The IC can implement PUF based on several physical factors, such as memory devices, logic delays, and resistors. The SRAM-based IC utilizes the unique random start state of the SRAM cell to generate a private key, which is safer since the state of the cell is erased when the power is turned off.
The second part of the problem can be solved with a public key infrastructure (PKI). A PKI is a system for creating, storing, and distributing digital certificates that are used to verify a particular public key belonging to an entity. The PKI creates a digital certificate, maps the public key to the entity, and securely stores the certificates in a central repository and abolishes them when needed.
In a PKI system, a Certificate Authority (CA) digitally signs its public key through the CA's own private key to authenticate all nodes. The most commonly used public key authentication format is X.509. When a device transmits a message digitally signed with its private key, the information can be verified using the device's public key. The device can also send its X.509 certificate to all nodes that receive its information so that all of these nodes have their public key. The receiving party can use the public key of the CA to verify the X.509 certificate including the public key of the device, and the CA public key is pre-placed in all nodes, which is an intrinsically trusted public key. Since the receiver can verify the signature used by the sender, this scheme can establish a proven hierarchical certificate trust chain. This solution also ensures that counterfeit machines are easily detected (Figure 2).
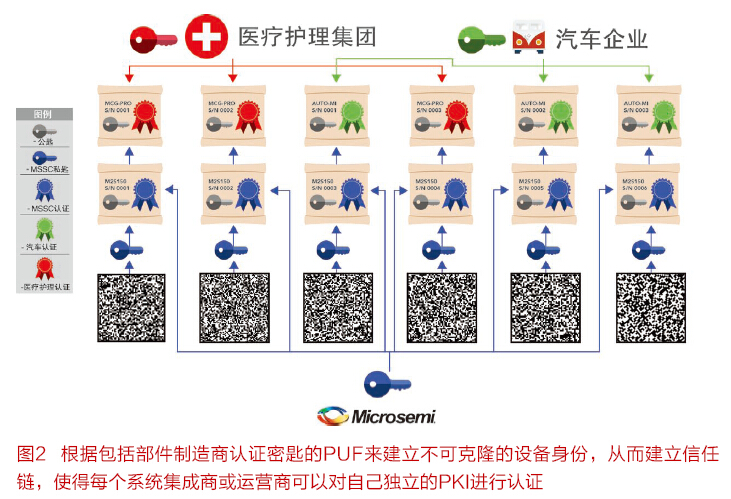
NHTSA believes that the public key infrastructure selection (asymmetric key) using the signature method is the most efficient way to implement communication security and trusted information delivery for a large number of users. In addition, in order to provide a secure network, PKI-based systems also provide an infrastructure that can be easily scaled with PKI solutions. Importantly, the effectiveness of this approach is highly dependent on the technical design decisions to implement this approach in a given environment. The V2X Certificate Authority issues a number of anonymous certificates per vehicle per year, blocking attempts to track owner actions.
Some devices can implement PKI using PUF technology. These devices offer a wide range of product roadmaps with a variety of I/O and fiber density options that allow users to select the device that meets their needs. The SRAM PUF in these devices utilizes device-level certificate authority to establish a pre-configured authentication identity for each node in the network. These devices also have built-in encryption capabilities, such as hardware accelerators for AES, SHA, HMAC, and Elliptic Curve Cryptography (ECC), as well as encryption level true random number generators. These features are also used in conjunction with the user's own certificate authority to create user PKIs or to register systems for use in V2X PKIs in the US or Europe.
Since malicious people can enter on-site systems, such as vehicles, it is important that the hardware be protected from various physical or side channel attacks such as differential power analysis (DPA). In addition to advanced key storage and key generation technologies, such as PUF and ECC, some devices also have a DPA-licensed license to provide SOC and FPGA with security, remote control, and DPA-renewable capabilities. DPA's patent license also allows users to accelerate PKI transactions in a DPA-secured manner using DPA countermeasures through a large amount of computing power in mainstream FPGAs. V2X networks protected by these solutions will ensure communication security.
Strain/flex Reliefs And Grommets
the power Connectors we provide overmolding solutions and modular tooling.
We also offer to the OEM and distributor users a diversified line of strain / flex reliefs and grommets, such as Solid, Solid-Rib, Uniflex, Multiflex, in standard off the shelf or custom designs.
Overmolding the power connectors offers significant opportunities for cable improvements with higher pull strength not available with conventional backshells. Our technical staff is ready to help you from design and prototyping to small production run, assistance, and training.
Our team is ready to help with any of the following power connectors projects: overmolding mini fit jr. and mini-fit sr. connectors, , overmolded cables with micro fit terminations, sabre molded cable asemblies, amp duac overmolded power connectors, mate-n-lock power cables, power connector overmolding services, power connector molding, design and prototype of power cables across the board, small run molded power connecotrs , molded cable manufacturing, overmolding connectors for any power applications
Strain Reliefs And Grommets,Flex Reliefs And Grommets,Cable Strain Reliefs,Cable Flex Reliefs,Cable Grommets,Molded Strain Relief
ETOP WIREHARNESS LIMITED , https://www.etopwireharness.com