How the Trojan works
A complete Trojan system consists of hardware, software and specific connection parts.
(1) Hardware part: The hardware entity necessary to establish a Trojan connection. Control side: the party that remotely controls the server. Server: The party that is controlled remotely by the controller. INTERNET: The network carrier for remote control of the server by the control end and data transmission.
(2) Software part: the software program necessary for remote control. Control program: The program used by the control to remotely control the server. Trojan program: a program that sneaks into the server to obtain its operating authority. Trojan configuration program: Set the Trojan program's port number, trigger conditions, Trojan name, etc., so that it hides more concealed on the server side.
(3) The specific connection part: the elements necessary to establish a Trojan channel between the server and the control terminal through INTERNET. Control terminal IP, server IP: the network address of the control terminal and the server, and also the destination of data transmission by the Trojan. Control port, Trojan port: namely the data entry of the control end and the server. Through this entry, the data can directly reach the control end program or the Trojan horse program.
Trojan horses such as hacking tools for network intrusion can be roughly divided into six steps from the process point of view. Below we will elaborate on the attack principles of Trojan horses according to these six steps. 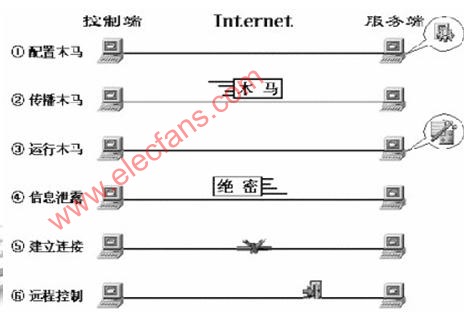
1. Configuration Trojan Generally speaking, a well-designed Trojan has a Trojan configuration program. From the specific configuration content, it is mainly to achieve the following two functions:
(1) Trojan camouflage: In order to hide the Trojan as well as possible on the server side, the Trojan configuration program will use a variety of camouflage methods, such as modifying icons, bundling files, customizing ports, self-destruction, etc. In detail in the section.
(2) Information feedback: The Trojan configuration program will set the information feedback method or address, such as setting the information feedback email address, IRC number, ICO number, etc., we will detail in the "information feedback" section Introduction.
2. Spread Trojan
(1) Transmission method:
There are three main ways of spreading Trojan horses: one is to send the Trojan horse in the form of an attachment through the E-MAIL, and the recipient will infect the Trojan as long as the attachment system is opened; the other is software download. Some unofficial websites bundle the Trojan with the software installation program in the name of providing software downloads. After downloading, as long as these programs are run, the Trojan will be automatically installed. The third is to use system vulnerabilities to install.
(2) Disguise:
In view of the harmfulness of Trojans, many people still have some knowledge of Trojans, which has a certain inhibitory effect on the spread of Trojans, which is unwilling to see Trojan designers, so they developed a variety of functions to disguise Trojan horses, in order to reduce user alertness and deceive users.
Trojan camouflage method
A. Modifying the icon can change the icon of the Trojan server program to HTML, TXT, ZIP and other file icons, which is quite confusing.
B. The masquerading method of bundling files is to bind the Trojan to an installation program. When the installation program runs, the Trojan secretly enters the system without the user's awareness. As for the files to be bundled, they are generally executable files (ie, files such as EXE and COM).
C. Anyone who has some Trojan knowledge knows that the error shows that if you open a file, nothing happens. This is probably a Trojan program. The designer of the Trojan is also aware of this defect, so there is already a Trojan that provides an error display. Function. When the server user opens the Trojan program, an error prompt box will pop up. The error content can be freely defined. Most of them will be customized into some information such as "the file is damaged and cannot be opened!". When the server user believes it is true, The Trojan quietly invaded the system.
D. Custom ports Many old Trojan ports are fixed, which brings convenience to determine whether the Trojan is infected. Just check the specific port to know what Trojan is infected, so now many new Trojans have added custom ports The user of the control end can choose a port between 1024 and 65535 as a Trojan port (generally not selecting a port below 1024), which brings trouble to the type of Trojan horse infected.
E. The function of self-destruction is to make up for a defect of the Trojan. We know that when a server user opens a file containing a Trojan, the Trojan will copy itself to the system folder (under the C: WINDOWS or C: WINDOWS \ SYSTEM directory). Generally speaking, the original Trojan file and the Trojan in the system folder The size of the file is the same (except for the Trojan that bundles the file), then the friend who has hit the Trojan can find the original Trojan file in the recently received letters and downloaded software, and then go to the system folder according to the size of the original Trojan to find the same size File, determine which one is the Trojan. The Trojan's self-destruction function means that after installing the Trojan, the original Trojan file will be automatically destroyed, so that it is difficult for the server user to find the source of the Trojan. It is difficult to delete the Trojan without the help of the tool to kill the Trojan.
F. Rename the Trojan. The file name of the Trojan installed in the system folder is generally fixed. So as long as you find some specific files in the system folder according to some articles about killing Trojans, you can determine what Trojan is in. So now there are many Trojans that allow control users to freely customize the installed Trojan file name, so it is difficult to determine the type of Trojan infected.
3. After the Trojan server user runs the Trojan or bundles the Trojan, the Trojan will be installed automatically. First copy yourself to the system folder (C: WINDOWS or C: WINDOWS \ SYSTEM directory), and then set the trigger conditions of the Trojan in the registry, startup group, and non-startup group, so that the installation of the Trojan is completed. After installation, you can start the Trojan:
(1) The activation of the Trojan by the trigger condition The trigger condition refers to the condition for starting the Trojan, which roughly appears in the following eight places:
A. Registry: Open the five primary keys under Run and RunServices under HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersion, and look for the key value that may be the startup Trojan.
B. Autoexec.bat and Config.sys: These two files in the root directory of the C drive can also start the Trojan. However, this loading method generally requires that the control user and the server establish a connection, and then upload the file with the same name that the Trojan startup command has been added to the server to overwrite the two files.
C. *. INI: the startup configuration file of the application program. The control terminal uses the characteristics of these files to start the program and uploads the file with the same name with the Trojan startup command to the server to overwrite the file with the same name, so that it can be achieved The purpose of starting the Trojan.
D. Registry: Open the HKEY_CLASSES_ROOT file type shellopencommand primary key and view its key value. For example, the home-made Trojan "Ice River" is to modify the key value under HKEY_CLASSES_ROOTtxtfileshellopencommand, and change "C: WINDOWS NOTEPAD.EXE% 1" to "C: WINDOWSSYSTEMSYSEXPLR.EXE% 1", then you double-click a TXT file, the original Using NOTEPAD to open files now turns into a Trojan horse program. It should also be noted that not only TXT files, the Trojan can be started by modifying the key values ​​of the start commands of HTML, EXE, ZIP and other files
E. Bundled files: To achieve this triggering condition, the control terminal and the server must first establish a connection through the Trojan, and then the control user uses the tool software to bundle the Trojan file with an application, and then upload it to the server to overwrite the original file , Even if the Trojan is deleted, as long as the application bundled with the Trojan is run, the Trojan will be installed again.
F. Startup menu: Under the "Start --- Program --- Startup" option, there may be a trigger condition for the Trojan.
4. Information leakage:
A well-designed Trojan has an information feedback mechanism. The so-called information feedback mechanism means that after the Trojan is successfully installed, it will collect some software and hardware information of the server, and inform the user of the control terminal through E-MAIL, IRC or ICO.
From this email, we can know some software and hardware information of the server, including the operating system used, system directory, hard disk partition status, system password, etc. Among these information, the most important is the server IP, because only get this parameter , The control end can establish a connection with the server
5. Establish a connection:
The establishment of a Trojan connection must first meet two conditions:
First, the Trojan program has been installed on the server;
The second is the control terminal and the server must be online.
On this basis, the control terminal can establish a connection with the server through the Trojan port.
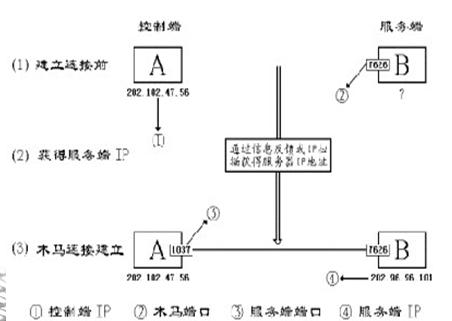
Machine A is the control terminal, and machine B is the server. For machine A to establish a connection with machine B, you must know the Trojan port and IP address of machine B. Since the Trojan port is set by machine A in advance, it is a known item. So the most important thing is how to get the IP address of the B machine.
There are two main methods to obtain the IP address of the B machine:
Information feedback and IP scanning. IP scanning, because the B machine is installed with a Trojan horse program, its Trojan port 7626 is open, so now A machine only needs to scan the host with the open port 7626 in the IP address segment, then A machine can pass the Trojan horse The control terminal program sends a connection signal to the B machine. The Trojan program in the B machine responds immediately after receiving the signal. When the A machine receives the response signal, it opens a random port 1031 to establish a connection with the B machine's Trojan port 7626. Only then is a Trojan connection established.
6. Remote control The control terminal program on the control end of the Trojan horse remotely controls the server through the Trojan horse program.
(1) Steal passwords: all passwords in the form of plain text, * or cached in CACHE can be detected by the Trojan. In addition, many Trojans also provide a keystroke recording function, which will record each tap on the server. The action of the keyboard, so once a Trojan invades, the password will be easily stolen.
(2) File operation: The control terminal can delete, create, modify, upload, download, run, change attributes and other series of operations on the server by remote control, which basically covers all file operation functions on the WINDOWS platform .
(3) Modify the registry: The control terminal can modify the server registry at will, including deleting, creating or modifying the primary key, subkey, and key value. With this function, the control end can prohibit the use of the server floppy drive and optical drive, lock the server's registry, and set the triggering conditions of the Trojan on the server to be more concealed.
(4) System operation: This content includes restarting or shutting down the server operating system, disconnecting the server network connection, controlling the server mouse, keyboard, monitoring the server desktop operation, viewing the server process, etc. The controller can even give The server sends information.
TWO FUNCTION : MCB AND RCCB FUNCTIONS
Residual Current Circuit Breaker With Over Load Protection
Residual Current Circuit Breaker,Residual Current Circuit Breaker with Over Load Protection 1p,Residual Current Circuit Breaker with Over Load Protection 2p
Wenzhou Korlen Electric Appliances Co., Ltd. , https://www.korlenelectric.com