With the advent of artificial intelligence and the Internet of Things era, data applications have become more frequent, and how should data security be protected? What are the software encryption algorithms, and in which aspects are these algorithms applied? Read it slowly and you will find the "small password" around us.
Symmetric encryption algorithmThe symmetric encryption algorithm is an early encryption algorithm and the technology is mature. In the symmetric encryption algorithm, the data sender sends the plaintext (raw data) together with the encryption key through a special encryption algorithm, and then sends it into a complex encrypted ciphertext. In the symmetric encryption algorithm, there is only one key used, and both the sending and receiving parties use this key to encrypt and decrypt the data, which requires the decrypting party to know the encryption key in advance. The characteristics of the symmetric encryption algorithm are that the algorithm is open, the calculation amount is small, the encryption speed is fast, and the encryption efficiency is high. The downside is that both sides of the transaction use the same key and security is not guaranteed. Symmetric encryption algorithms are more difficult to use on distributed network systems, mainly because of the difficulty in key management and high cost of use.
DES encryption algorithm
The DES encryption algorithm is a block cipher that encrypts data in packets of 64 bits. Its key length is 56 bits, and the same algorithm is used for encryption and decryption. The DES encryption algorithm keeps the key secret and exposes the algorithm, including encryption and decryption algorithms. Thus, only those who have mastered the same key as the sender can interpret the ciphertext data encrypted by the DES encryption algorithm. Therefore, deciphering the DES encryption algorithm is actually the encoding of the search key. For a 56-bit key, if the search is performed by an exhaustive method, the number of operations is 256.
With the continuous development of computer system capabilities, the security of DES is much weaker than it was when it first appeared. However, from the reality of non-critical nature, it can still be considered sufficient. However, DES is now only used for the authentication of legacy systems, and more to choose new encryption standards.
3DES encryption algorithm
3DES is a generic term for triple-data encryption algorithm block ciphers. It is equivalent to applying three DES encryption algorithms to each data block. Due to the enhancement of computer computing power, the key length of the original DES password becomes easy to be brute force cracked; 3DES is designed to provide a relatively simple method to avoid similar attacks by increasing the key length of DES. Not a new block cipher algorithm.
3DES is an encryption algorithm for DES to AES transition. The encryption algorithm is implemented as follows: Ek() and Dk() represent the encryption and decryption process of DES algorithm, K represents the key used by DES algorithm, M stands for plaintext, C stands for Cipher text, like this:
The 3DES encryption process is: C=Ek3(Dk2(Ek1(M)))
The 3DES decryption process is: M=Dk1(EK2(Dk3(C)))
AES encryption algorithm
The AES encryption algorithm is an advanced encryption standard in cryptography. The encryption algorithm uses a symmetric block cipher system. The minimum key length is 128, 192, and 256, and the packet length is 128 bits. The algorithm should be easy to implement in various hardware and software. This encryption algorithm is a block encryption standard adopted by the US federal government. This standard is used to replace the original DES and has been analyzed by many parties and widely used around the world.
The AES encryption algorithm is designed to support 128/192/256 bits (/32=nb) block size (ie packet length); 128/192/256 bits (/32=nk) password length is supported, in decimal Corresponding to 34×1038, 62×1057, 1.1×1077 keys.
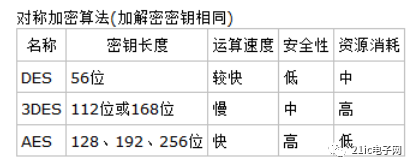
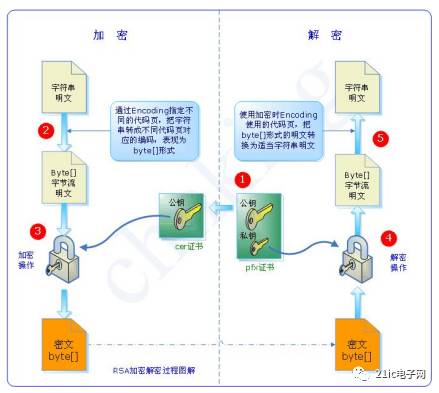
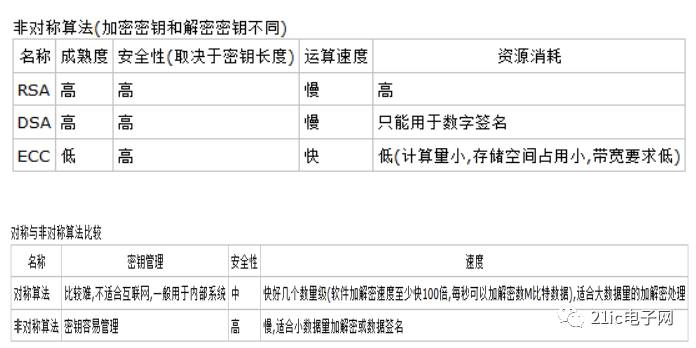
The asymmetric encryption algorithm uses two completely different but perfectly matched pairs of keys—public and private. When encrypting a file using an asymmetric encryption algorithm, the encryption and decryption process of the plaintext can be completed only by using a matching pair of public and private keys. Using the asymmetric encryption algorithm, before the sender and the receiver communicate, the receiver must send the public key that has been randomly generated to the sender, and retain the private key. Since the asymmetric algorithm has two keys, it is especially suitable for data encryption in distributed systems. The widely used asymmetric encryption algorithms are the RSA algorithm and the DSA proposed by the US National Bureau of Standards. Encryption technology based on asymmetric encryption algorithms is widely used.
RSA encryption algorithmRSA encryption algorithm is currently the most influential public key encryption algorithm, and is generally considered to be one of the best public key solutions. RSA is the first algorithm that can be used for both encryption and digital signatures. It is resistant to all password attacks known to date and has been recommended by ISO as a public key data encryption standard. The RSA encryption algorithm is based on a very simple number theory fact: it is very easy to multiply two large prime numbers, but at that time, but it is extremely difficult to factorize the product at that time, so the product can be exposed as an encryption. Key.
DSA is based on the integer finite-domain discrete logarithm problem, and its security is similar to that of RSA. An important feature of DSA is that two prime numbers are exposed, so that when you use someone else's p and q, you can confirm whether they are randomly generated or not, even if you don't know the private key. The RSA algorithm does not. DSA is just an algorithm. It differs from RSA in that it cannot be used for encryption and decryption, nor for key exchange. It is only used for signatures. It is much faster than RSA.
ECC encryption algorithmEllipse Encryption Algorithm (ECC) is a public key encryption system originally proposed by Koblitz and Miller in 1985. Its mathematical basis is to use the rational points on elliptic curves to form the computational difficulty of elliptic discrete logarithms on Abel addition groups. . Public key cryptosystems are generally classified into three categories according to the problems they are based on: large integer decomposition problem classes, discrete logarithm problem classes, and elliptic curve classes. Elliptic curve classes are sometimes classified as discrete logarithmic classes. The elliptic curve cryptosystem is one of the currently known public key systems, which provides the highest encryption strength for each bit. The best algorithm for solving the discrete logarithm problem on elliptic curves is the Pollard rho method, which has a time complexity of full exponential order.
The feature of the irreversible encryption algorithm is that the key is not needed in the encryption process. After the plaintext is input, the system directly processes the ciphertext through the encryption algorithm. The encrypted data cannot be decrypted, and only the plaintext is re-entered, and the same is repeated. The irreversible encryption algorithm processes the same encrypted ciphertext and is re-recognized by the system before it can be decrypted. The application of more irreversible encryption algorithms in computer networks includes the MD5 algorithm invented by RSA and the irreversible encryption standard SHS recommended by the US National Bureau of Standards.
MD5 encryption algorithmMD5 is a hash function widely used in the field of computer security to provide message integrity protection. A brief description of the MD5 encryption algorithm can be: MD5 processes the input information in 512-bit packets, and each packet is divided into 16 32-bit sub-packets. After a series of processing, the output of the algorithm consists of four 32. The bit grouping consists of cascading the four 32-bit packets to generate a 128-bit hash value.
MD5 is widely used for password authentication and key identification of various software. MD5 uses a hash function, and its typical application is to generate a summary of information for a piece of information to prevent tampering. A typical application of MD5 is to generate a fingerprin fingerprint on a Message to prevent it from being "tampered". If there is a third-party certification body, MD5 can also prevent the "rejection" of the author of the document. This is called the digital signature application. MD5 is also widely used in operating system login authentication, such as UNIX, various BSD system login passwords, digital signatures and many other aspects.
SHA1 encryption algorithmSHA1 is a message digest algorithm that is as popular as MD5. The SHA encryption algorithm mimics the MD4 encryption algorithm. SHA1 is designed to work with the Digital Signature Algorithm (DSA).
SHA1 is mainly applicable to the digital signature algorithm defined in the digital signature standard. For messages less than 2"64 bits in length, SHA1 will generate a 160-bit message digest. When a message is received, this message digest can be used to verify the integrity of the data. During the transmission, the data is likely to occur. Change, then this will generate a different message digest. SHA1 can not restore information from the message digest, and two different messages will not produce the same message digest. So, SHA1 can verify the integrity of the data, so say SHA1 is a technology for ensuring file integrity.
The SHA1 encryption algorithm can use no more than 264 bits of data input and produce a 160-bit digest. The input is divided into 512-bit blocks and processed separately. A 160-bit buffer is used to hold the middle and final results of the hash function. The buffer can be represented by five 32-bit registers (A, B, C, D, and E). SHA1 is an algorithm that is more secure than MD5. In theory, all digital verification algorithms that adopt the "message digest" method have "collision" - that is, the message digests calculated by two different things are the same, interworking This is the case with cheating. However, it is more difficult for a highly secure algorithm to find the "collision" of the specified data, and it is more difficult to use the formula to calculate the "collision". So far only MD5 has been cracked in the general security algorithm.
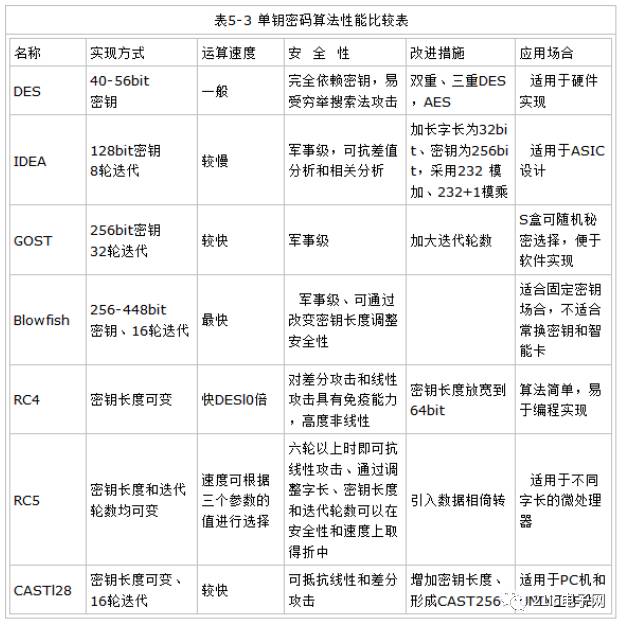
Of course, in addition to the above encryption algorithm, there are other methods, Xiaobian found a chart to supplement.
Our company specializes in the production and sales of all kinds of terminals, copper terminals, nose wire ears, cold pressed terminals, copper joints, but also according to customer requirements for customization and production, our raw materials are produced and sold by ourselves, we have their own raw materials processing plant, high purity T2 copper, quality and quantity, come to me to order it!
Copper Connecting Terminals,Cable Lugs Insulated Cord End Terminals,Pvc Insulated Cord End Terminal,Cable Connector Insulated Cord End Terminal
Taixing Longyi Terminals Co.,Ltd. , https://www.lycopperterminals.com